PKI vs FIDO
Both as PKI as FIDO are based on the same cryptographic algorithm — digital signature. As PKI as FIDO do use certificates. In case of PKI is is typically called qualified certificate and in case of FIDO Enterprise – attestation certificate.

The scheme explains the principle of “personal binding” – the qualified certificate links the personal data of the person and the cryptographic key of the electronic signature.
Based on the qualified certificate, a service is able to verify the signature and get a guarantee that the signature was made by the person who is responsible for using the specified key and who is mentioned in the qualified certificate.
In case of FIDO Enterprise the attestation certificate does not contain the personal data of an owner, but just a unique serial number of the Authenticator.
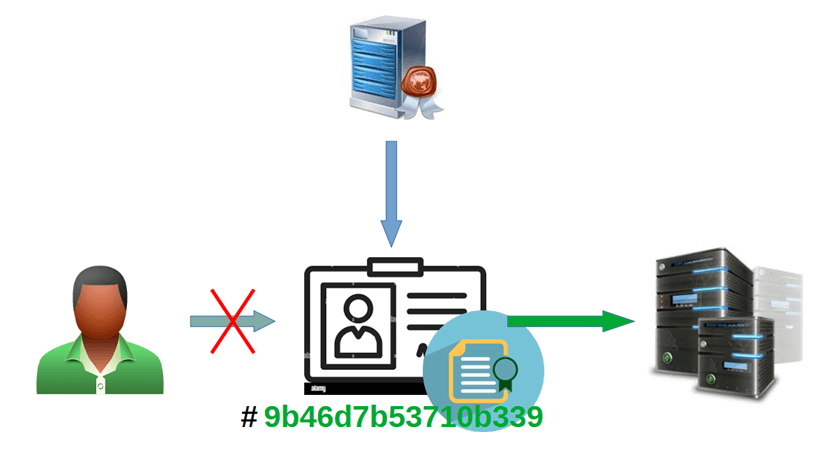
That is why the scheme is called “device binding”. The attestation certification does not contain any personal data of it’s owner.
Let’s consider how an Authenticator, which does support FIDO Enterprise ( CTAP 2.1), works.
The authenticator stores a predetermined list of enterprise servers – the “Green List”.
On the picture, the “Green list” contains servers with identificators 7bc4..2b9cdc та 5ecc…9d84ad. The identificators are correspond to the servers workspace.company.net and resources.company.net.
When authenticating with a server from this list, the authenticator returns its own attestation certificate containing its unique serial number. In this way, the server from the “green list” receives information about which access rights its owner should have.
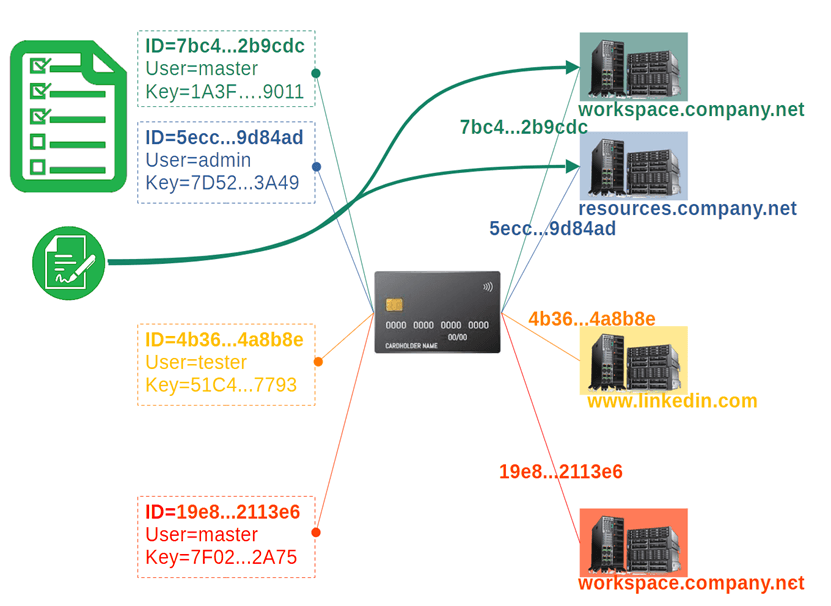
Based on the attestation certificate, a server from the “green list” is able to verify the signature and get a guarantee that the signature was made by the Authenticator which generated the key and which unique serial number is mentioned in the attestation certificate.
In such an indirect way the server get information, who was performed the authentication.